Smart Grid Telemetry, Data Key to Securing Distributed Energy Networks
Energy data has a key role in securing and protecting our energy future. As the global shift to decentralized energy networks keeps growing, together with the rising adoption rates of electric vehicles (EVs), cyber adversaries are finding an expanding array of opportunities to attack and exploit the dynamic energy sector.
By leveraging smart-grid energy telemetry and smart-grid data and fusing them into cybersecurity engines, operators could better detect, prevent, and mitigate the newly emerging cyber risks and attacks before any damage could be inflicted.
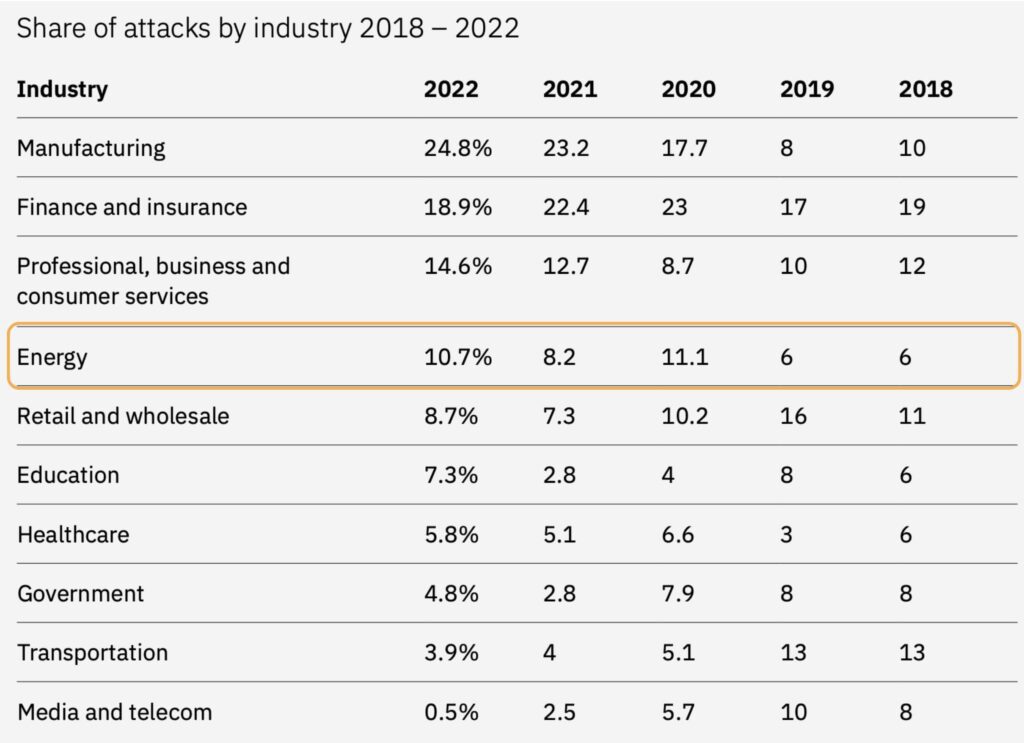
According to the Threat Intelligence Index report, the energy sector accounted for 10.7% of the
cyberattacks responded to by X-Force in 2022, positioning energy as the fourth-most targeted industry (Figure 1). In North America, energy firms experienced 20% of cyberattacks, making the energy sector the most frequently targeted industry. Moreover, the Russian invasion of Ukraine further increased concerns over cyberattacks on energy networks.
As new distributed energy networks, such as EV charging hubs (Figure 2), microgrids, substations, and distributed energy resources such as solar and wind, are getting more digitally advanced than ever before, they are becoming increasingly challenging to defend, with versatile and vast attack surfaces.
In recent years, new platforms and components, such as energy storage solutions, energy management systems, smart meters, EV chargers, solar panels, and smart inverters, have been introduced to distributed energy networks. Most of these components are connected directly to the Internet or to the cellular network, including to various cloud-based applications, to streamline telemetry signals and enable automated and remote
control over energy production, distribution, and consumption.
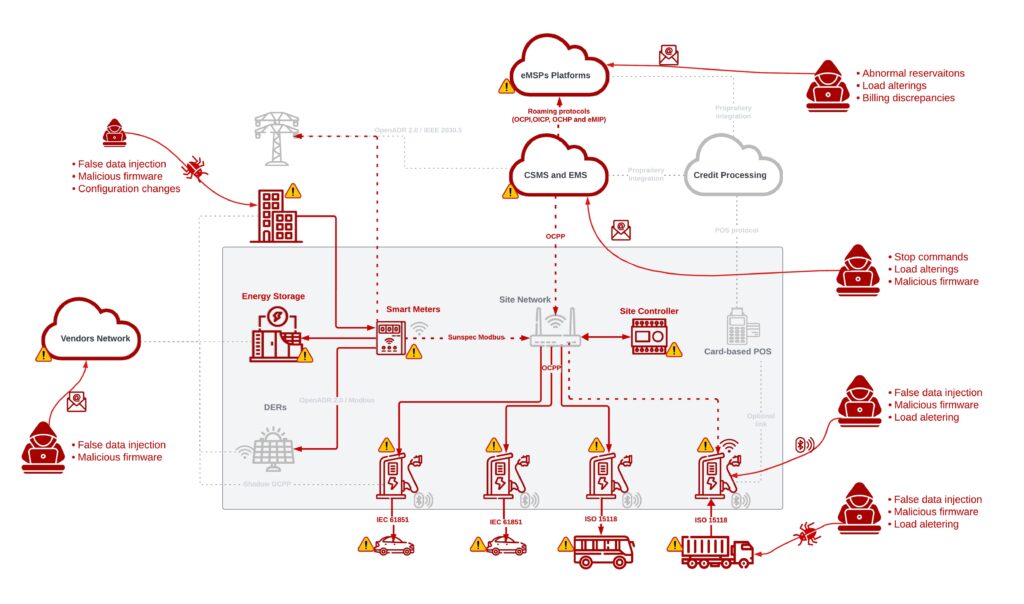
Various standards and technologies have already been developed and integrated into today’s distributed energy infrastructure such as the OCPP for smart EV charging, IEC 61850 for digital substations, and IEEE 2030.5 for smart energy profile applications. All utilize the innovations of IoT (Internet of Things), cloud, and data analysis to improve safety, increase productivity and efficiency, enhance revenue collection, and support the volatile demand and production of the new energy networks.
With more and more connected systems to monitor and secure, security teams are more likely to miss something, enabling attackers to infiltrate and exploit the network, causing widespread damage to the energy network and its users. As a result, we need to ensure that we have the right safeguards in place, ready to manage and face all of these risks.
A different cybersecurity approach is needed in order to mitigate the newly emerged risks without forfeiting the benefits of digitization, automation, and data-driven optimizations of distributed energy networks.
With this new array of systems, data points, management protocols, and energy telemetry signals comes great potential and opportunity for cybersecurity. Security teams could harness the new standardization and energy data points to boost their network security with increased visibility and advanced accurate detection to quickly mitigate cyberattacks before substantial damage can be inflicted.
Finding Cyber Attackers’ Fingerprints in Energy Networks
Most cybersecurity attacks on distributed energy networks have energy-related symptoms and side effects. If not monitored and analyzed correctly, these energy symptoms (Figure 3) could be experienced as mere maintenance issues. A hacked smart meter or inverter issuing false metering data will usually go unnoticed or undetected until it is already too late. A spike in energy due to energy theft will be rendered as a maintenance issue and so on.
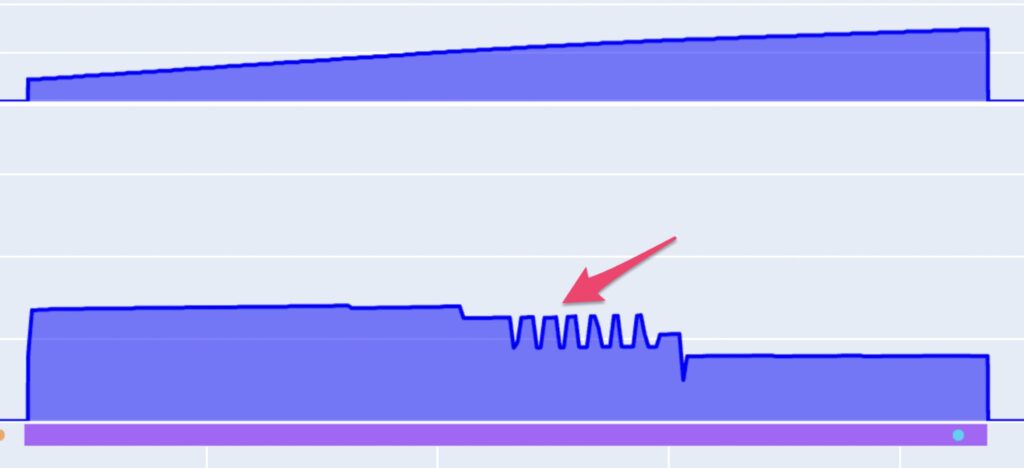
Cyber adversaries typically aim to achieve a specific goal or cause a specific type of damage via their attack. In distributed energy networks, these cyberattacks could manifest in various types of damage, including local grid blackouts, hardware damage, energy theft (in the case of EV charging), operational discontinuity (DoS/DDoS), local breakers tripping, and more.
It is crucial to detect and respond to cyber incidents as soon as possible. By incorporating smart grid and energy telemetry together with demand response (DR) and management protocols, new baselines could be provided for distributed energy networks. We could rapidly and accurately detect anomalies and suspicious activities, and react to cyber attacks before they begin.
Fusing Energy Telemetry With Cybersecurity
Does more data mean more problems, and is there a need for a contextualized approach? While leveraging energy data for the sake of better cybersecurity measures is important, the amount of energy data points being generated is immense. It could be a vicious cycle of introducing more systems and components that generate more energy data. To make sense of it all and enable data-driven actions, cybersecurity teams will need to be equipped with the precise tools and processes to respond measurably (minimizing false positives) and interact
with their counter operational teams in an effective manner.
Generalistic cybersecurity solutions, while important, lack the needed context, terminology, and know-how to detect energy-related symptoms of ongoing cyberattacks and could consequently increase dramatically the false-positive alerts or even the false-negatives. That could cause frustration and friction between the operational and cybersecurity teams. Moreover, too many false-positive alerts could cause alert fatigue, eventually rendering those systems useless and exposing these networks to cyberattacks.
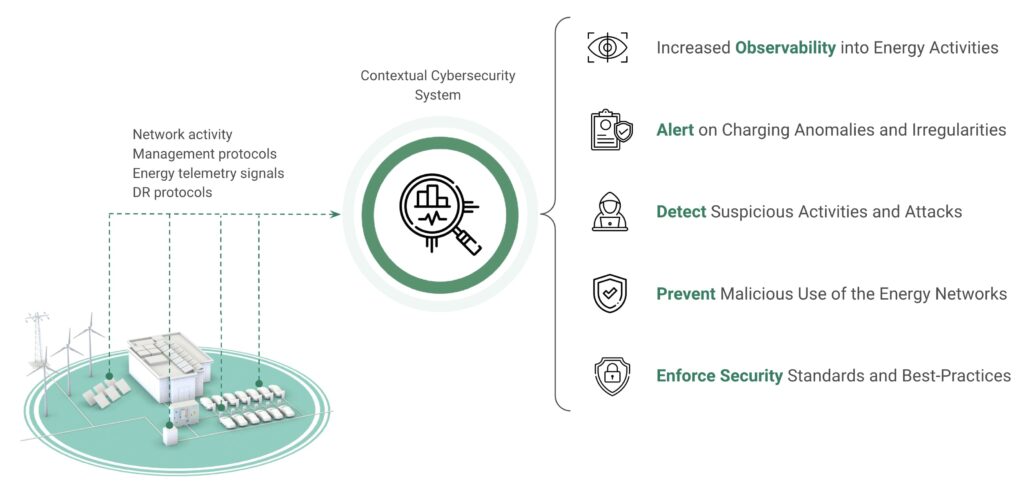
Integrating energy telemetry with cybersecurity engines (Figure 4) underscores the need for tailored cybersecurity solutions in the energy sector that incorporate and consider specific contextual factors and can rapidly and effectively detect and respond to attacks and suspicious activities.
The Benefits of Contextualized Cybersecurity
By adding context and energy telemetry into cybersecurity strategies and solutions, several
benefits emerge:
- Early threat detection: Contextualized cybersecurity can identify potential threats
early, allowing proactive mitigations as soon as possible, by integrating all energy data
points with DR and management protocols in the right context. - Reduced false positives: With a deep understanding of the network and components
operations, with their unique architecture and protocols, a contextualized cybersecurity
system will not trigger alerts on known but rarely seen operations, and reduce the
probability of alert fatigue. - Improved compliance: Energy companies must adhere to a multitude of regulations
and standards. Contextualized cybersecurity solutions can help meet compliance
requirements efficiently and effectively and enable the needed synergies between
operational and security teams. - Increase utilization: Energy companies can allocate resources more effectively by
prioritizing cybersecurity investments based on the unique risks they face. Contextualized cybersecurity measures bolster the resilience of energy infrastructure against targeted attacks, reducing downtime and ensuring a continuous energy supply.
The fusion of energy telemetry with cybersecurity heralds a new era of contextualized security in the energy sector. To protect against emerging threats and ensure the continuity, availability, and secure operations of the distributed energy networks and EV charging infrastructure, tailored contextualized cybersecurity solutions are no longer a luxury but a necessity. As the energy sector embraces this approach, it could harness the benefits of data-driven efficiency without compromising on security, ushering in a brighter, safer future for the energy landscape.
—Or Shwartz and Ron Tiberg-Shachar are co-founders and CPO and CEO, respectively, at SaiFlow, which provides a tailored cybersecurity solution for CP, EVSE, DER, and distributed energy networks, focusing on securing their standard protocols, such as OCPP, OCPI, IEEE 2030.5, DNP3, IEC 61850, and more. SaiFlow’s platform provides posture management, cyber monitoring, detection, and prevention abilities, all incorporating smart-grid and sensor data in establishing the baselines, correlations, and anomalies of these types of networks.